
Account Takeover Prevention: Stop ATO Before It Costs You Millions
Proactive credential monitoring stops ATO before attackers strike.
Average ATO incident costs $12,000. Here's how to stop them before they start.
TL;DR
Account takeover happens when criminals use stolen credentials to break into user accounts. The Verizon DBIR 2025 found that 31% of breaches last year traced back to stolen credentials.[1] This guide covers the full picture: how ATO actually works, what prevention looks like for enterprises vs. MSPs, how to wire it into your existing stack, and specific next steps you can take today. If you're using xonEnterprise+ for your own domains or xonThreatIntel+ for client monitoring, it all starts with one question: which of your credentials are already out there?
What ATO Really Costs Your Business
Money talks. Especially in budget meetings.
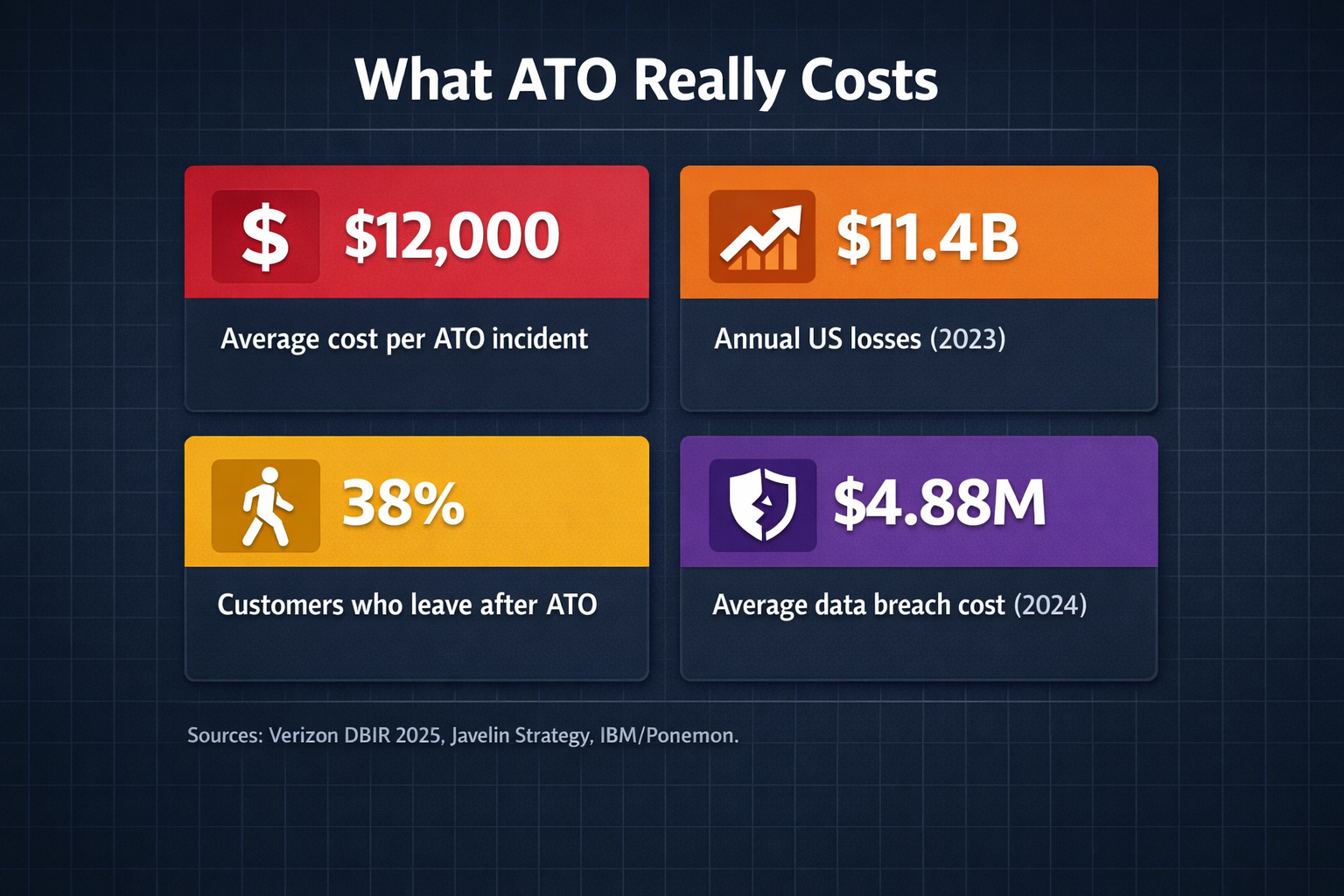
Javelin Strategy Research pegs the average ATO incident at $12,000.[2] That's one account. Not a breach, not a campaign. A single compromised login. Now multiply that across your org. Annual ATO losses in the US hit $11.4 billion in 2023,[3] and honestly? The trajectory isn't slowing down.
But the dollar figure only tells part of the story. What caught our attention in the research: 38% of customers who experience an account takeover leave and never come back.[4] Think about that for a second. You're not just losing money on the incident itself. You're hemorrhaging lifetime customer value. IBM and Ponemon put the average breach cost at $4.88 million for 2024.[5] The CFO cares about that number. So does the board.
This stopped being just a security team problem a while ago. It's a revenue problem, a retention problem, and increasingly a regulatory one too.
The ATO Attack Chain: Know Your Enemy
Before we get into solutions, you need to understand what you're actually defending against. Account takeover isn't one thing. It's a chain. And every link is a chance to break it.
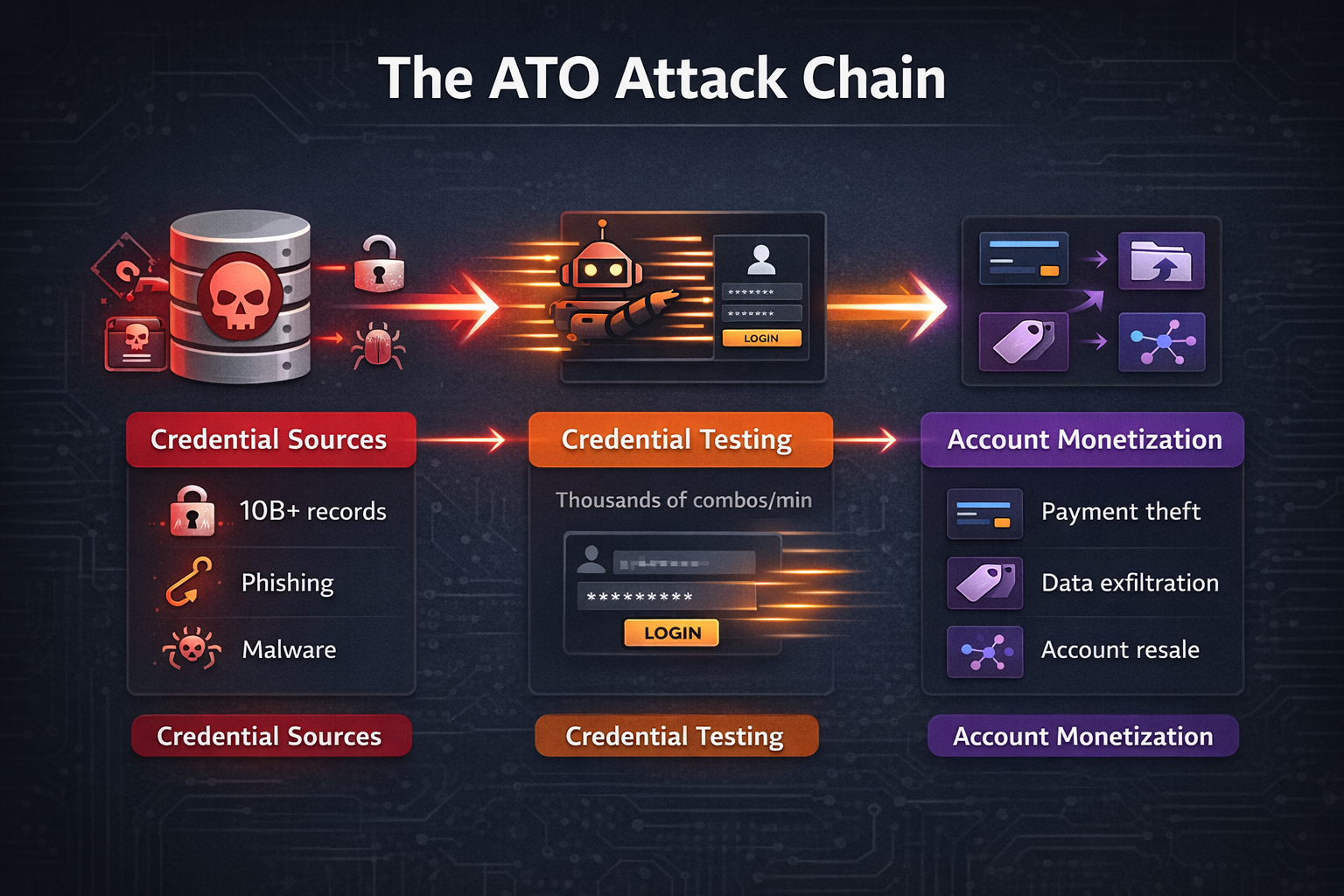
Where Stolen Credentials Come From
Here's what surprises people: attackers almost never hack your systems directly. Why would they? There are over 10 billion credential records already floating around from previous breaches. That pool gets bigger every week.
Phishing campaigns keep working embarrassingly well (we've seen organizations with robust training programs still get caught). Malware and infostealers quietly pull login details off infected machines. Dark web marketplaces sell credentials sorted by industry, geography, even job title. It's a supply chain problem, and the supply is enormous.
Our breach repository tracks over 660 confirmed breaches. New ones show up weekly. Each feeds the credential pool attackers draw from.
How Attackers Test Credentials
Once they've got a batch? Testing starts immediately. Automated stuffing tools rip through thousands of username-password combos per minute. The smarter attackers go low-and-slow, staying under rate limits, cycling through residential proxies so the traffic looks like a normal person logging in from home.
And that's the real problem with ATO detection. Your security tools see what looks like legitimate activity. Valid username. Correct password. Normal-looking IP. Without credential intelligence telling you that password showed up in a breach last week, there's nothing to flag.
What Happens After Takeover
Speed is the name of the game once an attacker gets in. They drain stored payment methods. Wire transfers go out. Data gets exfiltrated, creating compliance nightmares on top of the direct customer harm. Some attackers flip the accounts on underground markets, feeding the whole cycle again. Others use the foothold for lateral movement. One compromised account becomes five, then twenty.
That's what you're up against. Now let's talk about what actually works to stop it.
Real Results: Proof This Works
Technical details are coming. But first, does any of this actually work in production? Short answer: yes. Here are two real deployments.
Enterprise: Regional Healthcare Network
A healthcare network with 4,500 employees across 12 facilities had zero visibility into exposed credentials. After a phishing-driven ATO compromised an admin account and triggered a HIPAA review, their security team deployed xonEnterprise+ to monitor all corporate domains. The initial scan flagged 2,300 employee credentials already sitting in breach databases. Alerts were routed to Slack and their Sentinel SIEM, and batch password resets were triggered within hours.
Within 90 days:
Continuous monitoring now catches new exposures within minutes. Every breach alert auto-creates a ticket in ServiceNow and notifies the affected employee's manager via Teams.
MSSP Partner: Managed Security Provider
An MSSP managing 80 SMB clients had no breach monitoring in their portfolio. Analysts were manually checking HIBP one domain at a time. They deployed xonThreatIntel+ with all client domains onboarded in a single afternoon. The multi-tenant dashboard gave each client their own breach exposure view, and CXO reports were white-labeled under the MSSP's brand.
Six months later:
Breach monitoring became a high-margin add-on service. Three clients upgraded to larger security packages after seeing their exposure data for the first time.
Proactive domain monitoring. Concrete revenue impact. Those aren't projections. That's what happened. Let's dig into how.
Two Paths: Enterprise vs. MSP/Partner
How you roll out ATO prevention depends on a simple question: are you protecting your own people, or your clients' people? Different answer, different tooling.
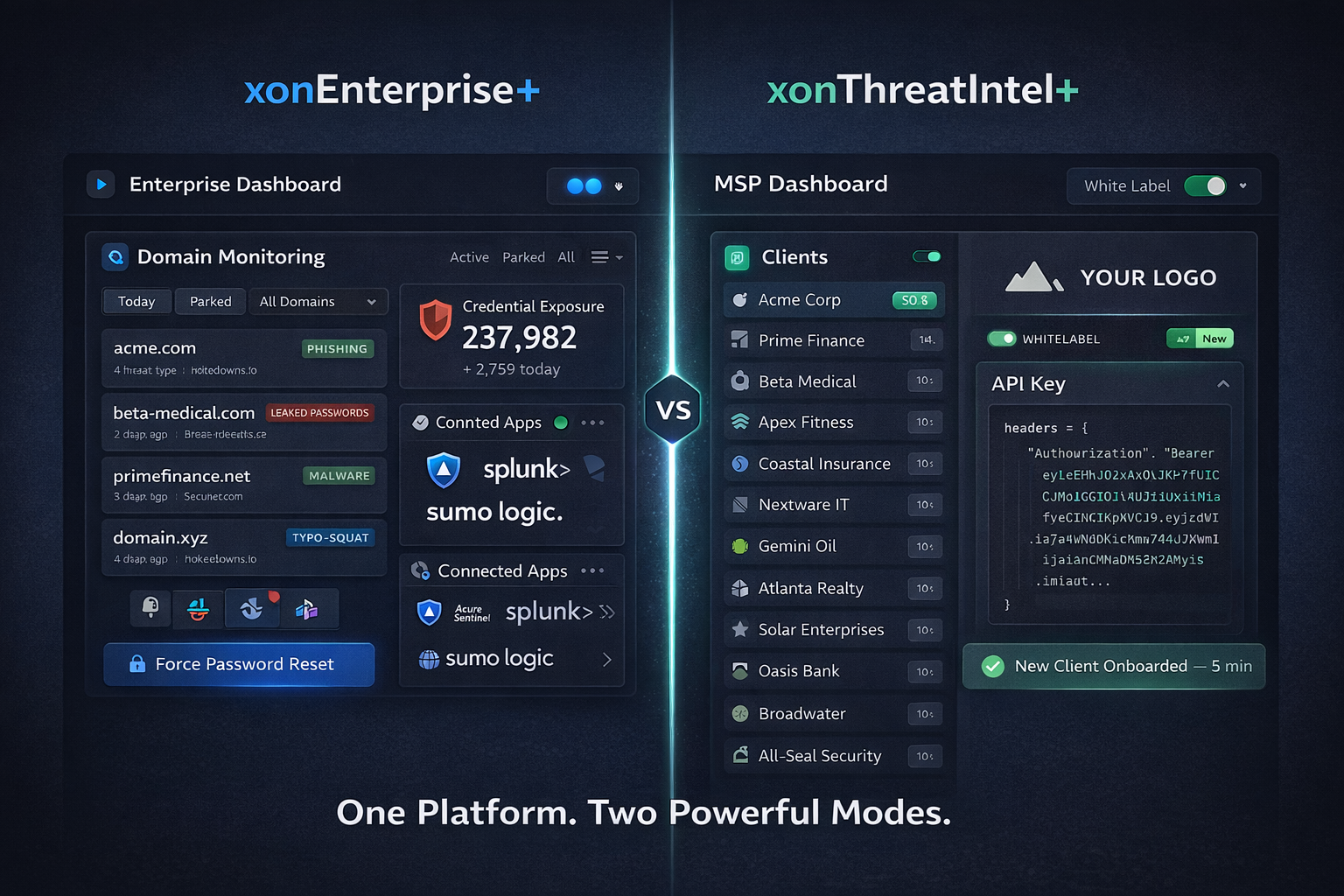
Protecting Your Own Organization
You're an enterprise. You've got employees, customers, corporate domains. xonEnterprise+ was built for exactly this scenario. It watches your email domains around the clock, runs real-time credential checks when employees log in, pipes events into your SIEM (Sentinel, Sumo Logic, Splunk, whatever you're running), pushes alerts to Slack, Teams, or email, and forces password resets the moment it finds exposed credentials.
The workflow is dead simple. xonEnterprise+ monitors. A breach drops with your employees in it. Alert fires. SIEM picks it up. Automation triggers a password reset. The user gets notified. Incident logged. Done. The whole thing runs without someone manually checking breach databases at 2 AM.
Protecting Your Customers
Different game if you're an MSP, MSSP, or security vendor. You're juggling dozens (sometimes hundreds) of client domains, and each one needs its data kept separate.
xonThreatIntel+ handles this with a multi-tenant dashboard where all your clients show up in one view. Each customer gets independent monitoring. White-label options mean you can slap your brand on the intelligence and deliver it as your own service. Full API access for automation. And volume discounts once you cross 50 domains, because at that scale, margins matter.
Onboarding a new client? Five minutes. Add their domains, and the dashboards get populated in under five minutes. No DNS verification, no ownership proof hoops. Configure alerts, done. Client protected.
From what we've seen, partners typically go to market one of four ways: bundle breach monitoring into an existing security package, offer it as a standalone premium tier, white-label the whole thing as their own product, or price it per-seat/per-domain to match their business model. Our step-by-step integration guide covers the full technical setup if you want the details.
Either path, same first move: figure out what's already exposed.
Are Your Users Already Exposed?
3,322 breaches happened in 2025 alone, a new record.[6] Your employees or customers are likely in at least one.
Takes 30 seconds. No signup needed.
Catching ATO Before the Damage
Half the battle is knowing an attack is underway. The other half? Knowing what to look for in the first place.
Red Flags in Your Auth Logs
Some patterns practically scream credential stuffing. Multiple failed logins followed by a success: that's someone testing passwords until one clicks. A new device paired with an immediate password change is another dead giveaway. Real users don't log in from a brand-new phone and immediately update their credentials. Attackers do.
Then there's geographic impossibility. New York at 2 PM, Singapore at 3 PM? That's not a frequent flyer. If someone changes both password and email in the same session, they're locking out the real owner. And multiple accounts hit from one IP? That's coordinated. Not a coincidence.
Behavioral Signals Worth Watching
Post-authentication behavior is where things get really interesting. A user who normally does 5 actions per session suddenly doing 50? Suspicious. Someone skipping their usual pages and going straight to account settings or payment methods? Worth investigating. Bulk downloads or API scraping patterns point to data exfiltration. And when a new shipping address shows up alongside a new card, that's a classic ATO play.
Each signal alone might be innocent. Stack three of them together and you've got a problem.
Detection matters. But honestly? Prevention matters more. Let's build those defenses.
Building Your Prevention Stack
One control won't cut it. Never has, never will. You need layers, each one catching what the others miss.
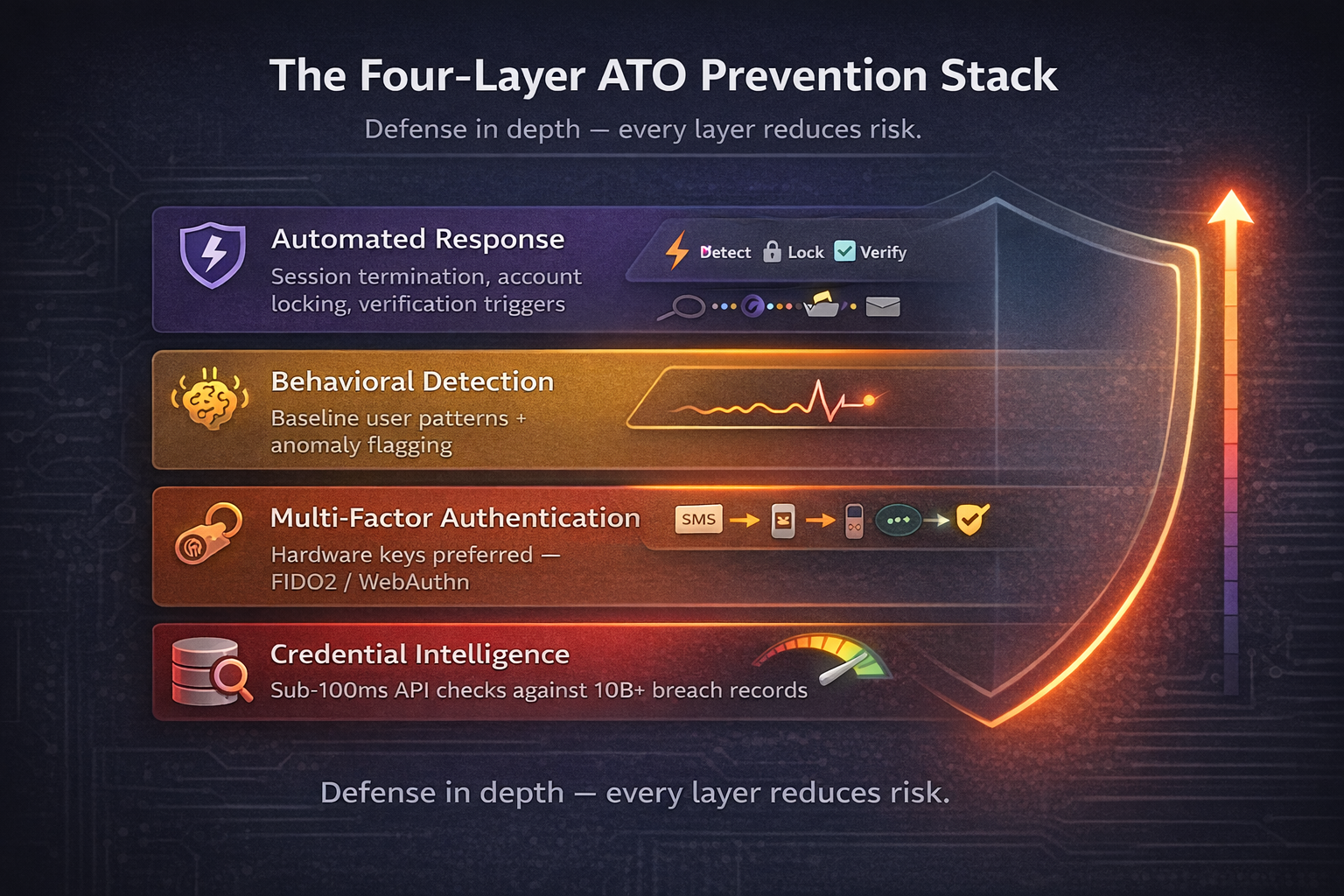
Layer 1: Credential Intelligence
People reuse passwords. You know this. We know this. Every awareness campaign in history hasn't fixed it. So instead of fighting human nature, work around it: find out when credentials show up in a breach before attackers get to use them.
The xonEnterprise+ and xonThreatIntel+ Breach Intelligence API indexes over 10 billion breach records. Responses come back in under 100 milliseconds. Uptime SLA sits at 99.99%. New breaches get indexed within 24 to 72 hours of disclosure, so you're not running checks against stale data from six months ago.
Here's what a domain-level breach assessment looks like in practice:
from xposedornot import XposedOrNot
# Breach Intelligence API key
xon = XposedOrNot(api_key="your-api-key")
def assess_domain_risk(domain):
result = xon.check_domain(domain)
exposed_count = result.metrics["exposed_emails"]
high_risk = result.metrics["high_risk_accounts"]
if high_risk > 0:
return {
"action": "force_reset_batch",
"accounts": high_risk,
"total_exposed": exposed_count
}
elif exposed_count > 10:
return {"action": "step_up_auth_domain"}
return {"action": "monitor"}Where should you plug this in? Registration (block passwords that are already breached), login (flag risky sessions), on a schedule (catch newly exposed credentials), and password change (stop people from rotating to another compromised password). That last one catches more issues than you'd expect.
Worth knowing: In our experience, the biggest ROI comes from continuous domain monitoring rather than one-off checks. xonEnterprise+ and xonThreatIntel+ watch your domains 24/7 and alert you within minutes of a new breach surfacing. Credentials can sit exposed for weeks before anyone notices. Continuous monitoring catches those before attackers do.
Layer 2: Multi-Factor Authentication
Credential intelligence identifies who's at risk. MFA makes sure a stolen password alone won't get anyone through the door.
Where to start? Admin accounts. Always. They're the highest-value targets in every organization. After that, extend MFA to financial actions: payments, withdrawals, anything touching money. Then cover account changes like password updates, email swaps, phone number modifications. Eventually you want it on everything, but those three tiers cover the critical stuff fast.
Quick note on MFA strength, because not all second factors are equal. Hardware keys (FIDO2, WebAuthn) are the gold standard and practically unphishable. Authenticator apps running TOTP are strong and widely adopted. Push notifications? Good UX, decent security. SMS codes are... better than nothing, but SIM swapping is a real thing. Pick the strongest option your users will actually use. An MFA method nobody enables protects nobody.
Layer 3: Behavioral Detection
So credential checks handle known exposures. MFA adds a second barrier. But what about the attacker who somehow has valid creds and can pass the MFA challenge?
That's where behavioral detection earns its keep. The idea: build a baseline of how each user normally behaves. When they log in, what devices they use, how they navigate, how long sessions last, which actions they take. When reality diverges from the baseline, you trigger step-up auth or flag it for human review.
We've noticed that behavioral detection catches the sophisticated attacks that blow right past the first two layers. Even with perfect credentials and a passed MFA challenge, an attacker's post-login behavior looks different from the real user's. They don't browse the way the account owner does. That gap is exploitable, in your favor.
Layer 4: Automated Response
Detection without action? Useless. And speed is everything here.
IBM/Ponemon 2024 says average breach detection takes 194 days.[5] One hundred and ninety-four days. For ATO, that's absurd. You need minutes. Maybe seconds.
Here's what a good automated response chain looks like: detection triggers an immediate session kill. Account locks. A notification goes out through a clean channel (not the potentially compromised email, and that detail matters). Identity verification is required before unlock. Credentials get forcibly reset. Then everything gets reviewed and logged forensically. No human in the loop for initial containment. Humans come in for the review, after the threat is neutralized.
Four layers. Each reinforcing the others. Now the question becomes: how does all of this connect to the tools already in your stack?
Plugging Into Your Existing Stack
Nobody wants a rip-and-replace project. Good news: this isn't one.
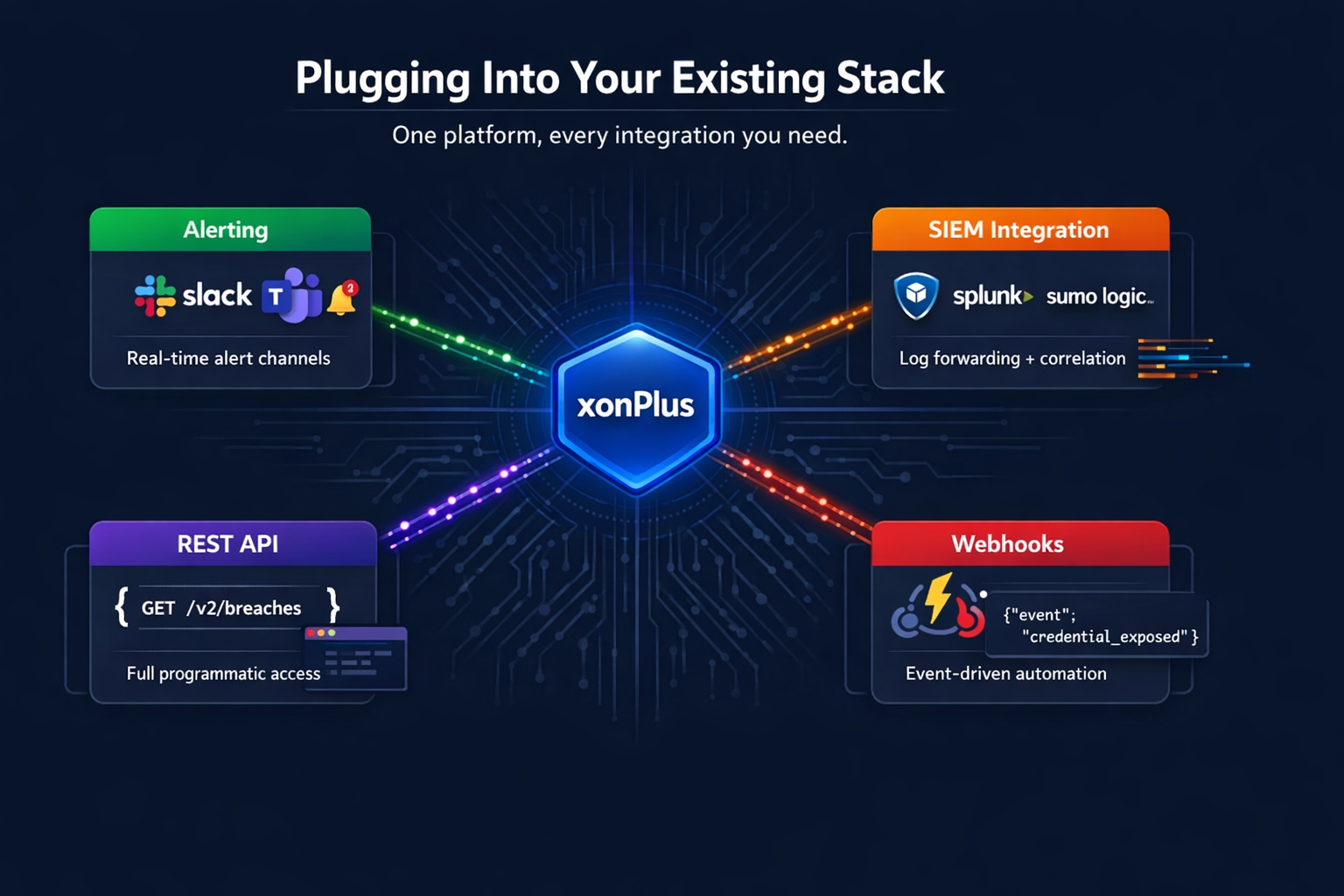
On the communication side, alerts land in Slack, Microsoft Teams, or email, wherever your team already hangs out. Developers get a REST API, Python SDK, Node.js SDK, and webhook support. Security ops can push breach events straight into Splunk, Azure Sentinel, or Sumo Logic for correlation with whatever rules and dashboards you're already running.
Integration takes minutes. Not days. Not a professional services engagement.
Azure Sentinel Example
If your SOC runs Sentinel, pushing breach events into Log Analytics looks like this:
def send_to_sentinel(breach_event):
workspace_id = "your-workspace-id"
shared_key = "your-shared-key"
body = {
"email": breach_event['email'],
"breach_id": breach_event['breach'],
"risk_level": breach_event['risk'],
"timestamp": breach_event['detected_at']
}
post_to_log_analytics(
workspace_id, shared_key, body,
"CredentialExposure"
)Slack and Teams Alerts
Alerts work best when they show up where your team is already talking. Here's a quick Slack webhook setup:
import requests
def alert_slack(breach_event):
webhook = "https://hooks.slack.com/services/YOUR/WEBHOOK"
message = {
"text": "Credential Exposure Detected",
"blocks": [{
"type": "section",
"text": {
"type": "mrkdwn",
"text": f"*Email:* {breach_event['email']}\n*Breach:* {breach_event['breach']}\n*Risk:* {breach_event['risk']}"
}
}]
}
requests.post(webhook, json=message)Want the full integration walkthrough covering API setup, SDK usage, and webhook configuration? It's all in our breach monitoring integration guide
Pricing and Compliance
What It Costs
Transparent pricing. No hidden per-query charges that blow up your bill.
xonEnterprise+ starts at $67/month for 1 domain, scales to 5 domains on Growth ($197/mo) and up to 25 on Ultimate ($497/mo). xonThreatIntel+ for MSPs starts at $499/month for up to 10 domains, with Growth ($1,299/mo) covering 25 domains and volume discounts kicking in at 50+. Every paid tier includes sub-100ms API response, 99.9% uptime SLA, and CXO dashboards. Full pricing breakdown here .
Security and Compliance
Privacy is baked into the architecture, not bolted on afterwards. Zero PII stored from your queries. Password checks use k-anonymity so actual passwords never leave your system. GDPR compliant across the board. For the full rundown on our infrastructure, WAF protections, rate limiting, and how we handle data, take a look at our security page.
Pro tip: If you're prepping for a SOC 2 or ISO 27001 audit, breach monitoring slots in as a proactive control. Auditors love seeing it because it demonstrates continuous monitoring rather than point-in-time checks.
For the compliance team, here's how breach monitoring maps to the frameworks you care about:
| Framework | Relevant Controls |
|---|---|
| SOC 2 | CC6.1 (Logical Access), CC7.2 (Monitoring) |
| ISO 27001 | A.9.4.3 (Password Management), A.12.4.1 (Logging) |
| NIST CSF | PR.AC-1 (Identity Management), DE.CM-3 (Monitoring) |
| PCI DSS | 8.2.3 (Password Requirements), 10.2 (Audit Trails) |
| HIPAA | 164.312(d) Authentication, 164.312(b) Audit Controls |
Your Implementation Roadmap
You don't need to boil the ocean. Here's a practical timeline that front-loads quick wins while building toward a mature program.
| Timeline | Actions |
|---|---|
| Today |
|
| This Week |
|
| This Month |
|
Real talk: Most teams we work with hit meaningful ROI somewhere in the "This Month" phase. The healthcare network above found 2,300 exposed credentials on day one. The MSSP added $18K in monthly recurring revenue within six months. You don't need a fully mature program to start seeing results.
Ready to Stop ATO?
The numbers: $12K per incident, 38% customer churn, 194 days average detection.
The proof: 2,300 credentials caught before exploit. $18K new MRR for an MSSP in six months.
Need enterprise pricing, partner programs, or custom integrations? Reach out at [email protected].
Questions Security Teams Ask
References
- Verizon 2025 Data Breach Investigations Report (DBIR)
- Javelin Strategy & Research, 2024 Identity Fraud Study
- Javelin Strategy & Research, Annual Identity Fraud Study
- Mitek Systems, Account Takeover Fraud Statistics
- IBM / Ponemon Institute, Cost of a Data Breach Report 2024
- ITRC 2025 Annual Data Breach Report
